Becoming A W200 Holder
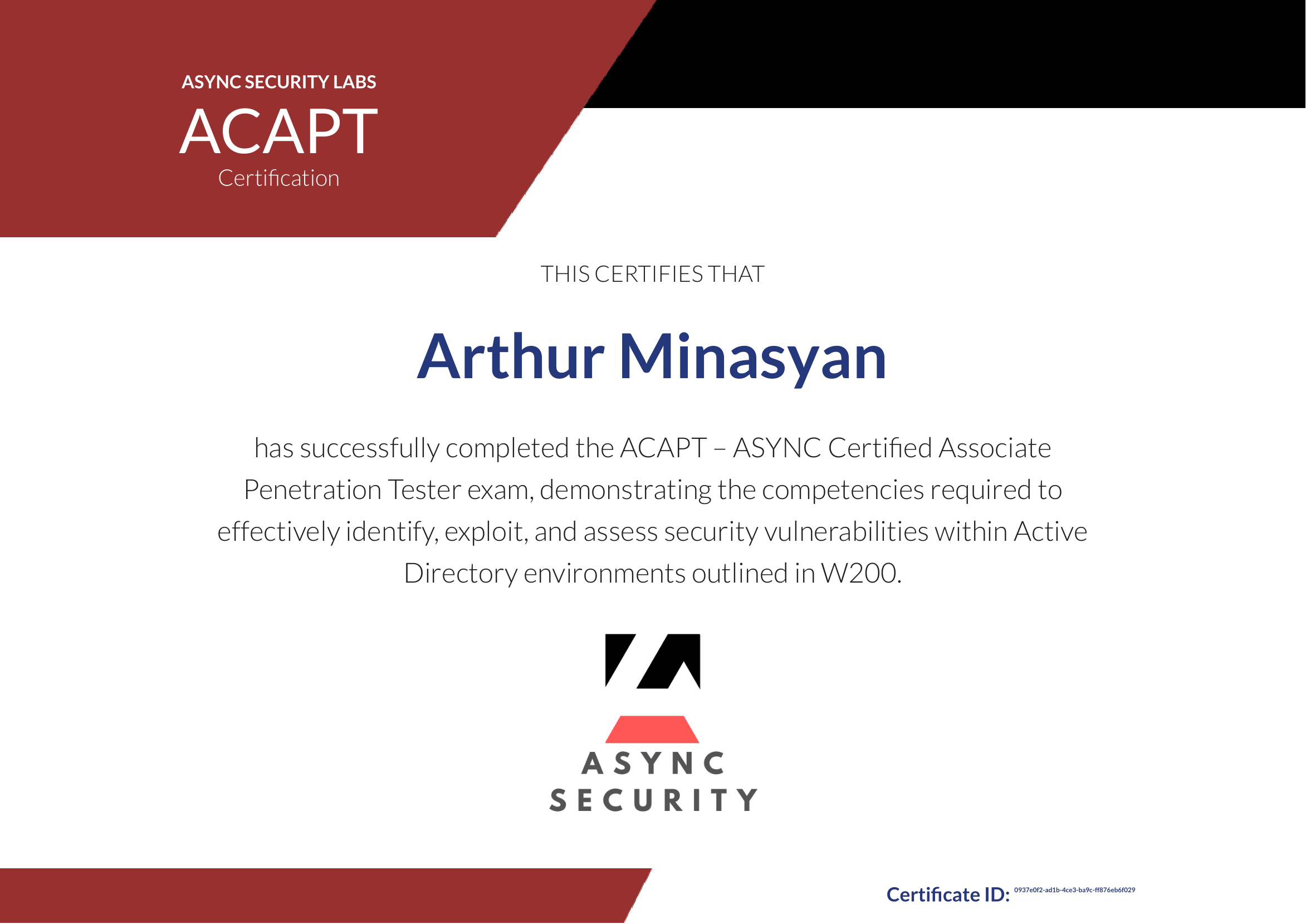
About a month ago I passed the W200 exam, making me the first ACAPT holder in the world. Even though the certification is not (yet) well-known, I’m still pretty proud of it. After passing, I received quite a number of messages asking me about the exam: how it was, whether it’s worth it or if I simply liked it. So instead of repeating myself again and again, I figured out I’d write a blog post about it. So…here we go again ^^
Again, I’m not sponsored by Async Security or any other vendor. This review is my honest opinion about the exam.
Who and what?
Async Security Labs is a Singapore-based company offering penetration testing and red teaming services. They also provide training, including the “W200” course and its corresponding certification, the “ACAPT” (Async Certified Associate Penetration Tester).
I’ve already written a full course review in my previous blog post, which you can find here. But to sum it up: the W200 focuses on Active Directory penetration testing, covering topics that many other vendors overlook (like attacking Linux AD joined machines). I found the course to be excellent (especially in terms of price-to-content ratio) and one of the best beginner-to-intermediate Active Directory pentesting courses available.
Preparation
The best way to prepare for the W200 is.. well, by doing the course itself obviously! The training material is literally ALL YOU NEED to pass the exam. There’s no shortcut though, you need to fully understand why you’re doing something and when to apply it. A methodical approach is needed to understand the full course material, but if you commit to it, you’ll come out with an extremely good baseline for Active Directory pentesting.
However, if you feel you need more material beyond the course, I recommend reading blog posts and write-ups from the community. Personally, I learned some great tricks just from Async Security’s own CTF write-ups. Of course, there are plenty of other highly skilled researchers sharing their knowledge as well. Here are some of my favorites (there are too many though..):
- https://blog.async.sg/
- https://gatari.dev/posts/ad-linux/
- https://www.thehacker.recipes/
- https://mayfly277.github.io/
- https://vuln.dev/
- …
One last very important point is that you should absolutely avoid approaching the exam as a regular CTF. You’re going to have an extremely hard time if you do so. Treat the exam as a real pentest instead. This mindset shift will help you A LOT!
The Exam
One day before the start of the exam, you’ll receive a VPN pack by email from the Async team, which won’t be activated yet. On the exam day, you’ll then receive the ROE (Rules of Engagement) and a reporting template, which will come in handy later. Here is some general info about the exam:
| Duration | Report required? | Proctored? | Number of hosts to compromise | Points required to pass |
|---|---|---|---|---|
| 24 hours practical exam + 24 hours reporting time | Yes | No | 4 | 80 |
Structure
The environment itself is very small: you have only four machines to compromise. And still..the exam was one of the best designs I’ve seen so far. It was extremely realistic, meaning that everything you encounter could genuinely happen in a real pentest. I don’t recall any exam being this realistic.
Despite the small environment, the lab will challenge your understanding of Active Directory. You need to be comfortable with authentication protocols (Kerberos, NTLM), with privilege-escalation techniques, and with a solid enumeration methodology. I struggled at some points and genuinely thought I might not make it. Don’t get me wrong: the exam is fair and very well designed, but it does require a strong understanding of the course material. Don’t underestimate it like I did at the beginning.
The exam also has some very unique aspects that I haven’t seen before. Because it mimics a real penetration test, you need to be careful with disruptive actions: anything that could impact a user account, a group, or other business-critical elements. For example, modifying a user password is considered disruptive, since the user would no longer be able to log in. If you need to perform such actions, it’s important to revert the changes before the exam ends. Failing to revert them will result in a deduction of points (more info later).
The second unique aspect is the remediation requirement. The remediation portion is extremely important for the report and is required to pass. Each remediation provides 10 points. I really liked this aspect because, in a real-world scenario, the customer is often left with the final report, so it’s important to provide clear guidance and help as much as you can.
Realistically, if you’re comfortable with Active Directory you can finish the exam in about 8–9 hours. It’s explicitly designed to NOT take the full 24 hours.
Points, Points, and Points
So, I mentioned points earlier and all those unique aspects—how does that work? Glad you asked!
The ROE you receive provides enough information to give you an idea. To pass, you need at least 80 points. You earn these points in two ways: by compromising machines and by writing remediations.
The “pwning” part adds up to 60 points, meaning each machine you fully compromise earns 15 points. To claim those 15 points you must fully compromise the host, which includes obtaining admin access.
So, if you compromise all four machines, you earn 60 points (4 × 15).
As mentioned before, the remediation portion adds up to 40 points total, with each remediation worth 10 points. This means you could pass the exam with combinations such as:
- Pwn all machines (60 pts) + 2 remediations (20 pts)
- Pwn three machines (45 pts) + 4 remediations (40 pts)
Remember: if you perform disruptive actions, you can lose points. It’s very important to revert all changes before the exam ends.
An important note: you can avoid point deductions even if you fail to revert a change, provided you document everything. Clearly explain what you did, why you did it, and why you weren’t able to revert the change. This gives you a chance to pass, although I wouldn’t recommend relying on this. Treat the exam as a real penetration test for a real client.
Finally, if you crash the domain controller (or really any critical resource) or attack the company’s router, your exam will be immediately terminated and marked as a fail. Be mindful of the scope, just as you would in the real world!
Reporting
I found the reporting window more than sufficient. The template provided by Async, although a bit goofy (I love it! :D), helps you structure your report and gives a good idea of how to build your own.
Basically, just follow this schema:
- Introduction, Objectives, Requirements, etc.
- High-Level Summary
- Recommendations
- Tools Used
- Scope
- Walkthrough
- From USER A to HOST B
- Explanations, blabla
- Remediations
- From HOST B to USER C
- Explanations, blabla
- Remediations
- From USER C to GROUP A
- Explanations, blabla
- Remediations
- …and so on
- From USER A to HOST B
- Cleanup
Of course, you can modify this however you like. This is simply the approach I used.
Did I Like It?
Hell yeah. As mentioned earlier, I found this to be the most realistic penetration-testing exam I’ve taken. Every action you perform, the way you compromise the machines, move laterally between hosts, mirrors techniques I’ve used in real engagements. Many other exams let you do almost anything, like freely modifying GPOs, user and group properties, or even entire OUs. In the real world, that can have serious consequences, so you need to be careful not to disrupt the business. I loved that this exam enforces that realism.
This might sound intimidating, but it really isn’t. If you’ve fully absorbed the course material, you can absolutely pass. I enjoyed the entire experience and had a lot of fun. The lab environment was also extremely stable, even with me testing from Germany / France while the infrastructure was in Singapore.
Overall, this exam is a genuine step up in your skill set. If you finish it, you’ll be ready to tackle real-world Active Directory penetration tests.